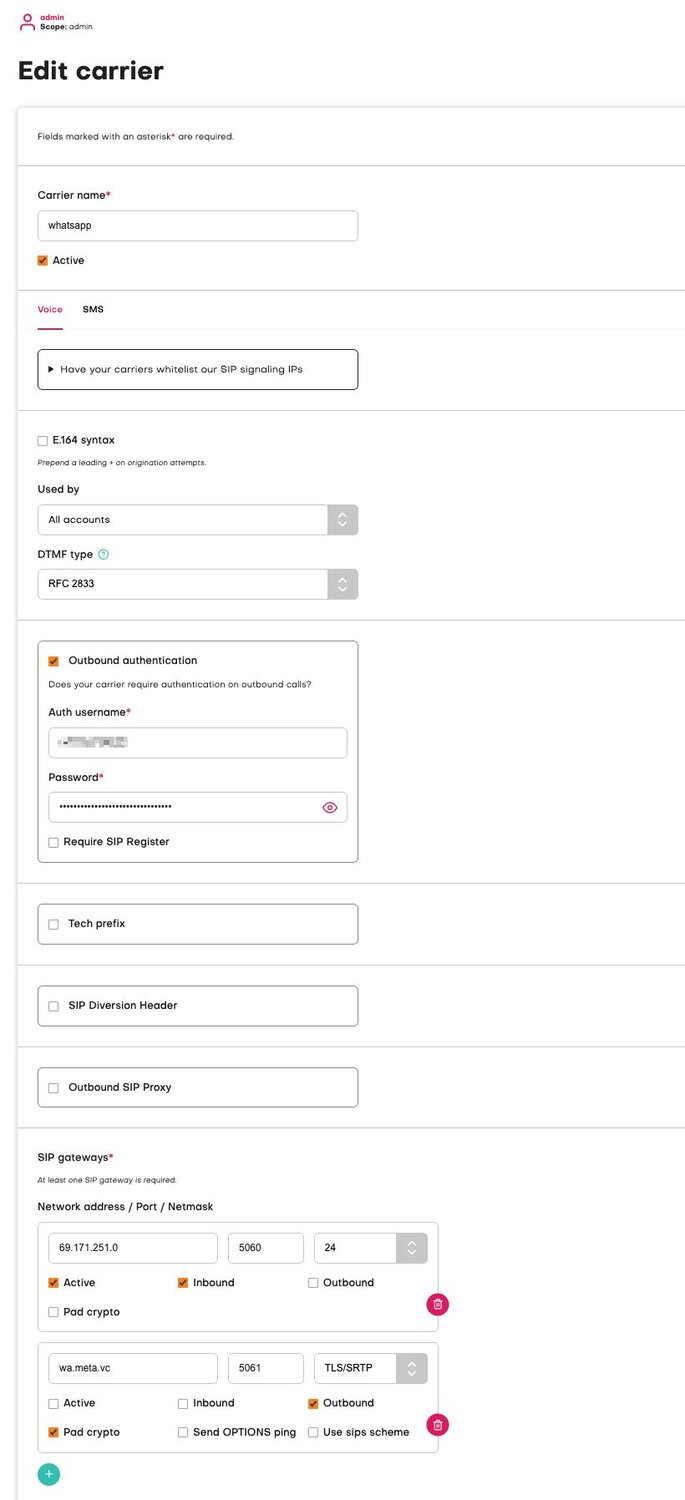
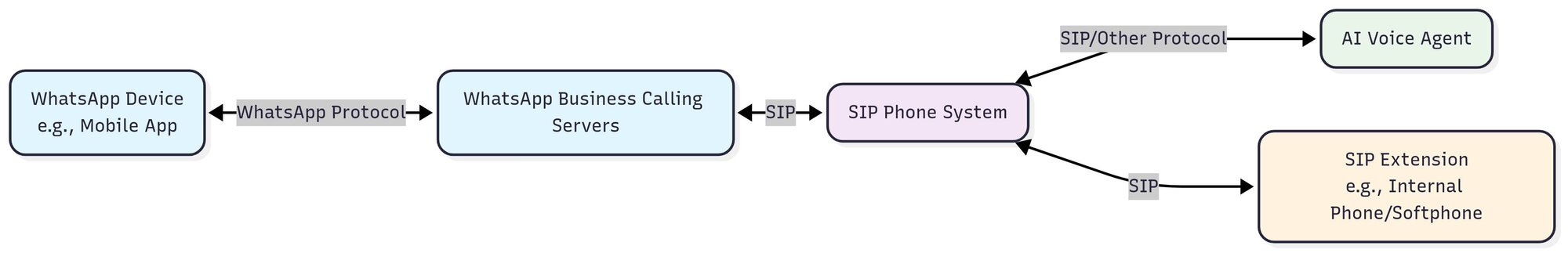
Notice the X-FB-External-Domain: wa.meta.vc header; this is a useful way to identify whether the call is coming from WhatsApp to get into the right configuration inside PJSIP.
If you want to go further, you can validate calls against the published IP ranges (docs). The catch: there are a lot of them (1001 ranges at time of writing), which makes it unwieldy to maintain in a PBX config. This may be required if your VoIP platform doesn’t support authentication challenges on inbound SIP.
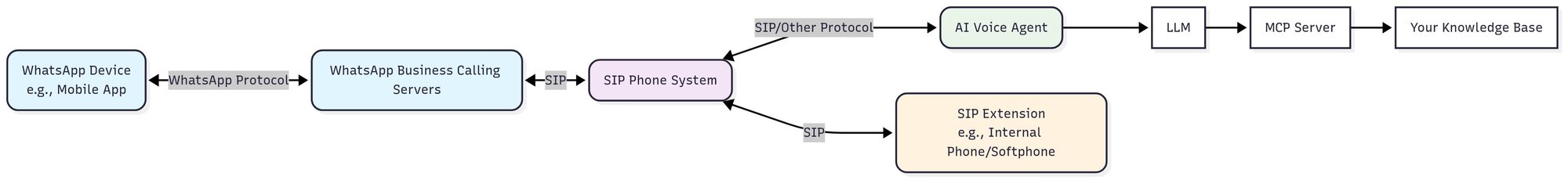
Jambonz Setup
Jambonz can work with WhatsApp Business Calling, but there are some important quirks you need to know.
1. No inbound SIP authentication
Jambonz doesn’t currently support authentication challenges on inbound SIP, so you can’t just rely on user/pass like you can with Asterisk. That leaves you with two options:
- Manually maintain the current 1001 IP ranges that WhatsApp publishes, or
- Start by letting the inbound traffic hit your SBC logs, see which IPs are denied, and add those incrementally - which is far from a foolproof way of doing this… but gets you to a point of receiving calls quickly.
Neither is perfect… until Jambonz gains inbound auth support, this is the reality.
2. Patch for media anchoring
You’ll also need to apply a patch we submitted to the Jambonz project to ensure media is anchored correctly: PR #1310. (You also need to set the anchor environment variable on your jambonz feature server process.
3. Carrier settings
Your carrier config in Jambonz needs some careful setup:
- Outbound auth is required using the details given to you during SIP setup.
- You must set an “active” network address for inbound - see the note above about setting these up.
- For outbound, use wa.meta.vc with the port 5061 with TLS/SRTP and pad crypto enabled.
You also need to set the register_from_domain setting but you can’t really do this in the UI without unintended consequences. If you don’t set this via the API, outbound calls won’t work correctly.

![![Placeholder: table of SIP/media requirements]](/blog/images/5ff38f61539f43b4a4b9c8dd6e2929b0.jpg)